Introduction
In this article, we will discuss something that aims to handle high traffic and ensure high availability in any application called Load Balancers.
As any web application grows in size and complexity, so does its demand for scalable and reliable infrastructure. Load Balancers help achieve this by distributing workloads evenly across networks and ensuring that applications do not get overwhelmed with requests and are running as efficiently as possible.
It is one of the most straightforward methods of scaling out an application infrastructure and it does so by using an effective traffic routing algorithm to distribute workloads evenly.
Sounds pretty fancy? No worries, we will go through everything about Load Balancers in detail in the upcoming sections
So keep reading
What are Load Balancers?
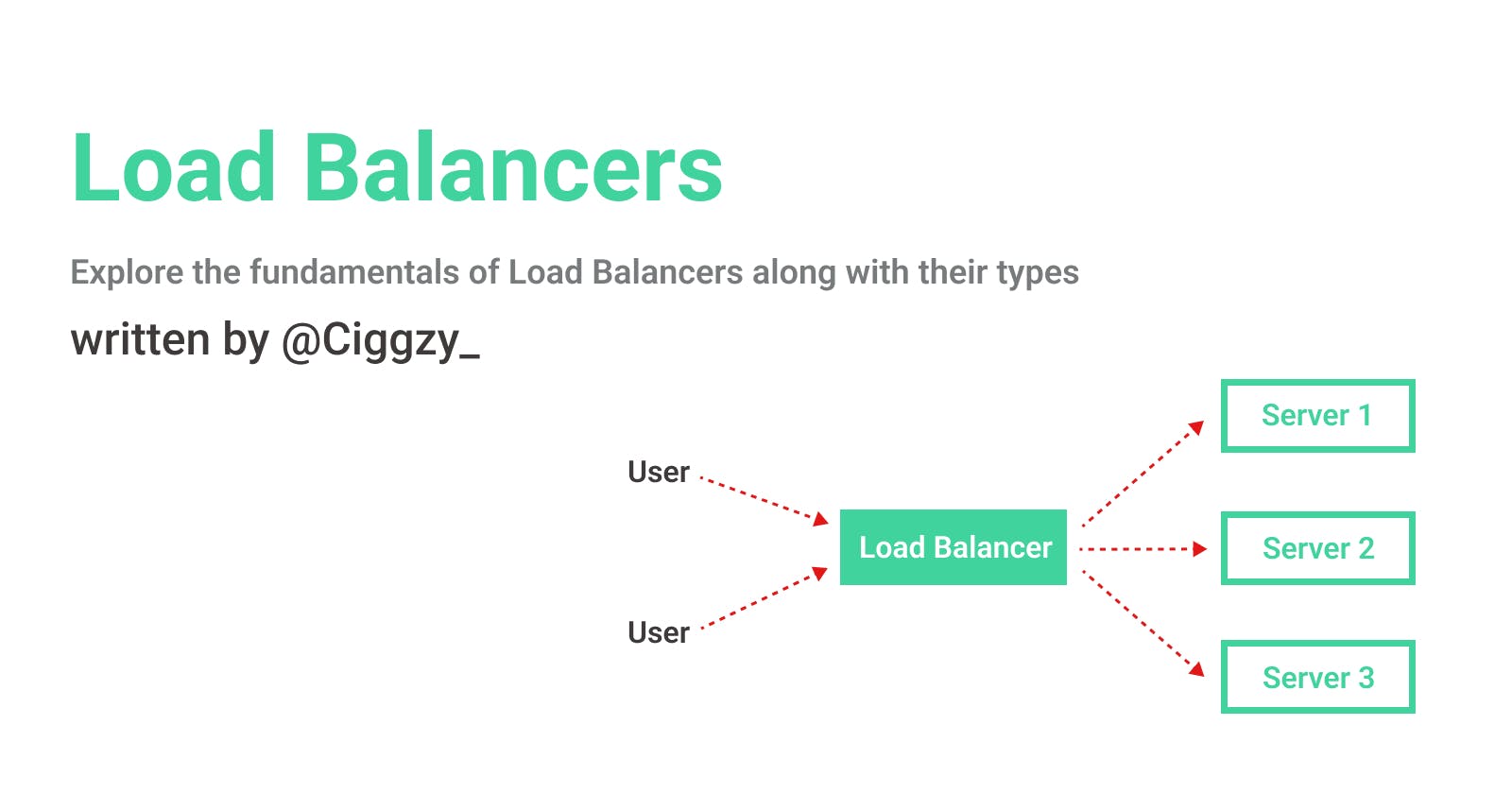
Load balancers are system-specifically designed network devices that distribute incoming traffic across multiple servers. They usually sit in front of the cluster of servers and use algorithms to determine the amount of traffic that should be routed to each server or service. In this way, they not only distribute the workload but also helps to optimize resource utilization and maintain minimum response time and maximum throughput which ensures that the services are not overwhelmed by requests and are running as efficiently as possible.
Let us now see an example to understand it in a better way
Imagine you own an e-commerce website that receives a large number of requests from customers to purchase products. If all of these requests were directed to a single server, that server would quickly become overwhelmed and unable to handle the traffic. This will result in the users facing downtime which is not what we want. To prevent this, a load balancer can be used to distribute the requests evenly across multiple servers, so that each server only has to handle a portion of the total traffic.
The load balancer will act as a gatekeeper, directing incoming traffic to different servers based on various factors such as the server's current load, its geographic proximity to the user, and the type of request being made. This helps to ensure that the system can handle the traffic and provide a fast and reliable experience for users.
Types of Load Balancers
Depending upon the Layer of the OSI model they operate at, load balancers can be of 2 types
Network Load Balancer / Layer 4 Load Balancer:
Based on the network variables like IP address and destination ports, Network Load Balancers distribute traffic at the transport level through the routing decisions. Such Load Balancers operate at TCP i.e. level 4 and do not consider any parameter at the application level like the type of content, cookie data, headers, locations, application behavior, etc. Performing network addressing translations without inspecting the content of discrete packets, Network Load Balancers care only about the network layer information and direct the traffic on this basis only.
Application Load Balancer / Layer 7 Load Balancer:
Ranking highest in the OSI model, the Application or Layer 7 Load Balancer distributes the requests based on multiple parameters at the application level. A much wider range of data is evaluated by the L7 load balancer including the HTTP headers and SSL sessions and distributes the server load based on the decision arising from a combination of several variables. This way Application Load Balancers control the server traffic based on individual usage and behavior.
Load Balancing Algorithms
We now know that Load Balancers work by distributing incoming traffic across multiple servers to improve system efficiency. But how exactly do they do it?
Under the hood, a Load Balancer decides on which server to forward the incoming request or traffic to based on a set of rules or algorithms called Load Balancing Algorithms. Once the Load Balancer has decided on which server to forward incoming traffic to, it establishes a connection with that server and forwards the incoming traffic. The server then processes the request and sends the response back to the load balancer, which in turn forwards the response back to the client.
Let us discuss some of the most important and common Load Balancing Algorithms
Round Robin
In the Round Robin algorithm, requests are distributed among a group of servers in a circular order. Each new request is sent to the next server in the list, and once the last server is reached, the algorithm starts again at the beginning of the list.
Least Connection
The least connection algorithm selects the server with the least number of active connections at the moment when a new request arrives. This algorithm is suitable when there are large differences in server capacity or when some servers may be overloaded.
IP Hash
In the IP Hash algorithm, the IP address of the client is used to calculate which server to send the request to. The algorithm uses a hash function to generate a unique number for each client IP address, which is used to select the server.
Weighted Round Robin
The Weighted Round Robin algorithm assigns a weight to each server in the pool, which corresponds to its capacity or processing power. Requests are then distributed based on the weights of the servers. Servers with higher weights receive a larger share of the traffic.
Least Response Time
The Least Response Time algorithm distributes requests based on the server's current response time. The server with the lowest response time is selected to handle the next request. This algorithm is suitable for applications where response time is critical.
Randomized
The Randomized algorithm distributes requests randomly among the servers in the pool. This algorithm is simple to implement and works well when there is no significant difference in the servers' capacity or when the traffic load is light.
These are some of the most common types of Load Balancing algorithms used in modern networks. Different Load Balancing algorithms can be used depending on the specific needs of the application or network architecture.
Benefits
Improved Scalability
Load Balancing helps to ensure that incoming traffic is distributed evenly among multiple backend servers. This helps to prevent any single server from becoming overwhelmed and ensures that the application remains highly available even during periods of high traffic.
Increased Availability
Load Balancers provide high availability by automatically redirecting traffic to another server if one server fails. This helps to ensure that the application remains available even in the face of server failures.
Better Resource Utilization
Load Balancing helps to ensure that all servers are utilized efficiently by directing incoming traffic to the server with the most available resources.
Enhanced Performance
Load Balancing helps to improve the performance of web applications by minimizing response time and maximizing throughput.
Choosing the right load balancer
While choosing the right Load Balancer for your application there are a few factors that need to be kept in mind, they are as follows
Traffic Volume
The amount of incoming network traffic your system receives is a crucial factor to consider. Some load balancers may be better suited for high-volume traffic, while others are better suited for low-volume traffic.
Scalability
Your load balancer should be able to scale with your system. Make sure you choose a load balancer that can handle additional backend servers as your system grows.
Protocol Support
Different load balancers support different protocols, such as HTTP, HTTPS, TCP, UDP, and more. Make sure you choose a load balancer that supports the protocols your system uses.
Health Checking
Load balancers should regularly check the health of backend servers to ensure they are still functional. Make sure the load balancer you choose has adequate health-checking mechanisms.
Load Balancing Algorithm
Different Load Balancing Algorithms can be used to distribute traffic, such as round-robin, least connections, IP hash, and more. Choose a Load Balancing Algorithm that suits your system's requirements.
Security
Security should be a top priority for any load balancer. Ensure that the load balancer you choose provides the necessary security features, such as SSL/TLS encryption, DDoS protection, and more.
Cost
Load balancers can vary in price depending on the features and capabilities they offer. Consider your budget and choose a load balancer that provides the features you need at a reasonable cost.
Conclusion
I hope you have enjoyed reading this article and if it helped you in any way do share and leave your feedback.
Thank you for reading and good luck scaling your application and distributing your network traffic using the above-mentioned traffic cop